Using ES Helper
ES Helper
ES Helper is purpose-built application focused on improving Enterprise Security deployments. Enterprise Security (ES) is a very expansive tool, and it brings in a lot of complexity that Admins may not have time to properly investigate and understand. With ES Helper, Admins will quickly know how well their Enterprise Security is being supported with actionable data. With the Utilization Score, and then with our Data Model Report, users can quickly find their next prioritized task for improving their score and their deployment.
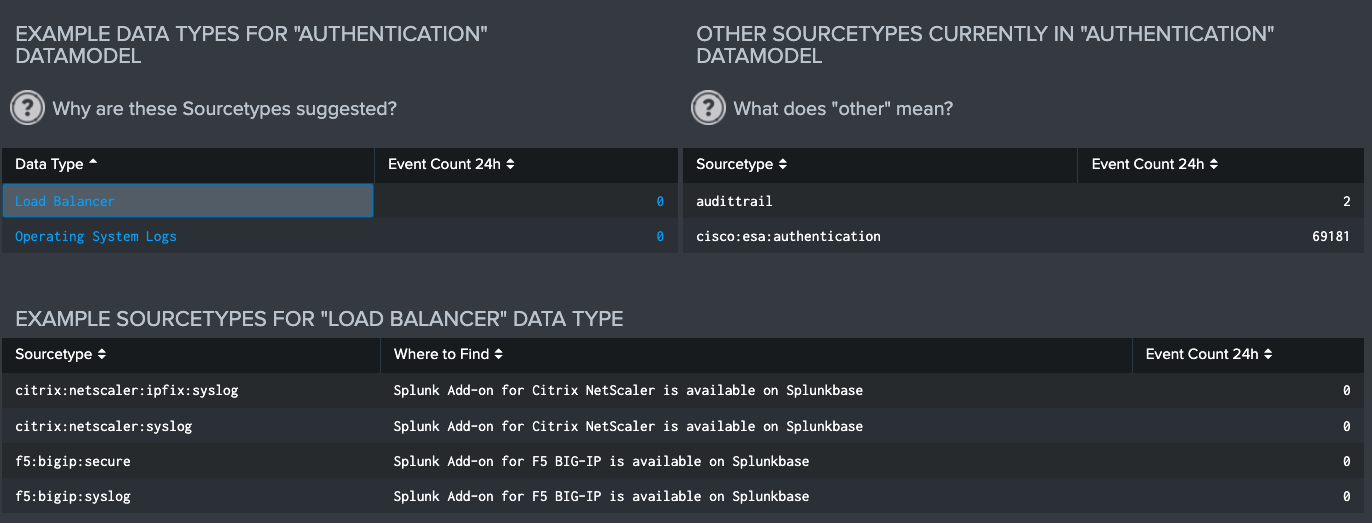
Utilization Score
The ES Utilization Score analyzes the Data Models that power ES and applies our priority-based model to produce a Utilization Score. This priority model is based on a deep investigation on how Enterprise Security utilizes the different data models, and from expertise on what ES outcomes are more actionable and important than others. Users can select the help text to see how their score was calculated.
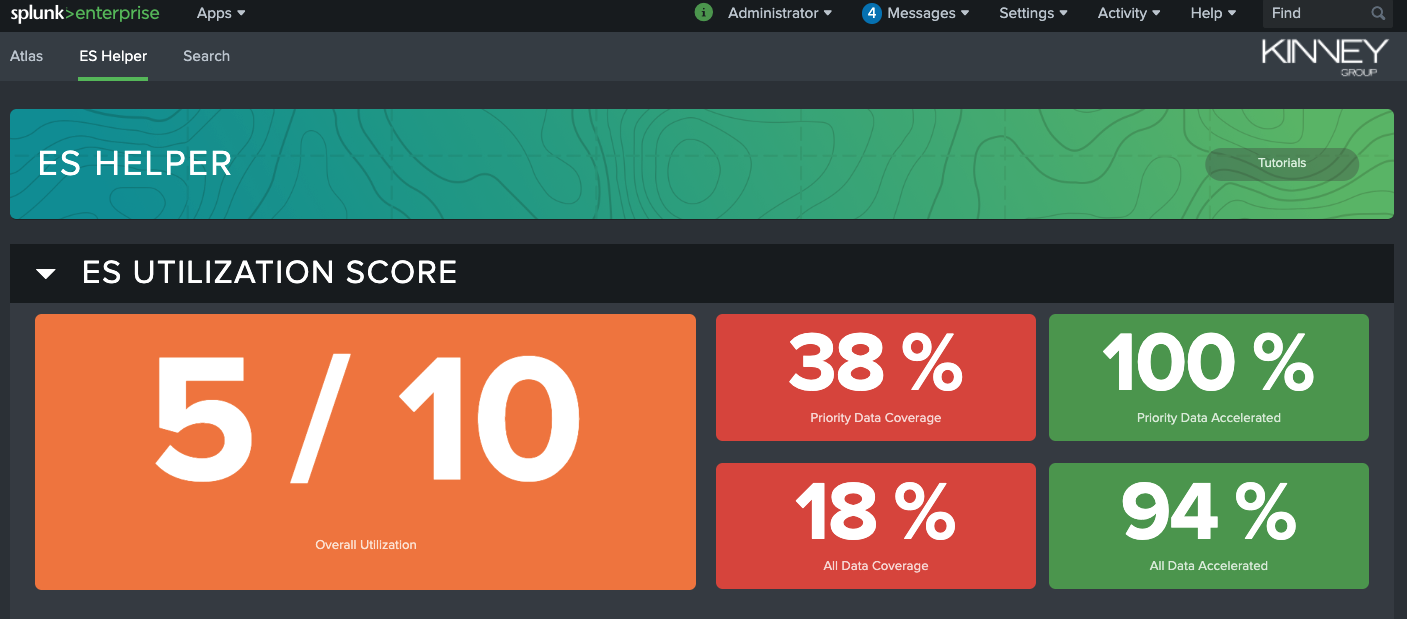
Data Model Report
Scrolling down, a user can see what is powering the ES Utilization Score. The ES Data Model Report shows all data models that feed into Enterprise Security. Users can identify a data model that doesn’t have any, or little, data and select it for recommendations. For instance, in the above example, the Change Data Model lacks any data, making it a prime subject for further examination. By selecting the Change Data Model, the reports below start to populate.
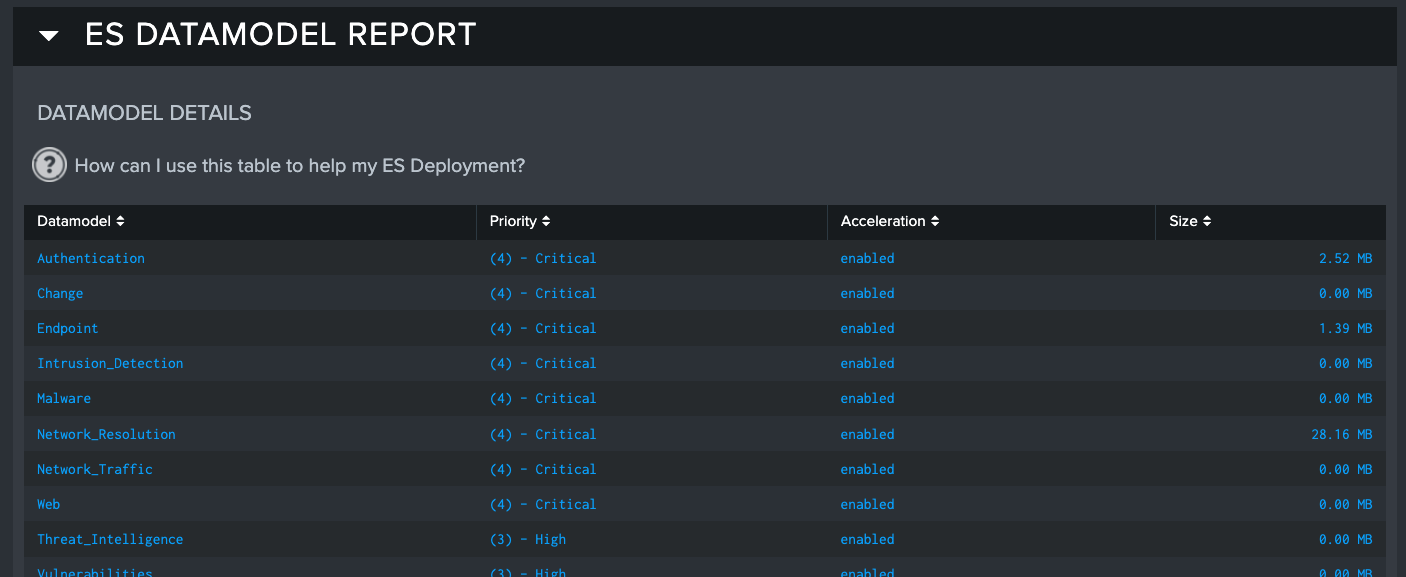
After selecting the Data Model, recommendations will start populating below. These recommendations contain source types that Atlas believes users should pursue for improving that data model’s representation in Enterprise Security. Adding this CIM compliant data to the ES System will update the report to show the Data Model is being filled with actionable data. Filling a high priority Data Model will improve the ES Utilization Score, and of course increase ES Deployment coverage and ability to deliver results in improving security posture and monitoring.